Configuring EAP
There are only a few steps required to configure EAP in FreeRADIUS Version 2 and later versions. First, create the "snake oil" certificates. These certificates have the proper form, if not the proper content.
$ make
OpenSSL requirements.
These certificates can be used for testing authentication, but they cannot be used in a production environment. For the purpose of the simple tests in this document, they are good enough.
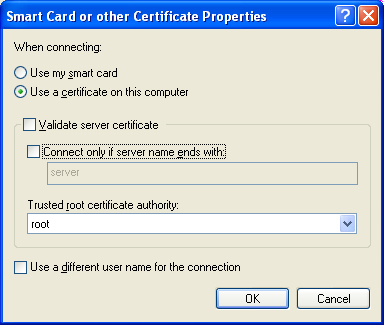
Next, configure 802.1X authentication for this SSID. On Windows, you will need to un-check the Validate Server Certificate option in the 802.1X supplicant (e.g. Windows laptop) strictly for testing. Other supplicants (e.g. Mac OSX, or wpa_supplicant) use different methods for permitting the use of an unknown certificate. See their documentation for more information.
Note that this checkbox has been removed in recent versions of Windows.
For command line testing, see eapol_test.
Start the server using radiusd -X, and wait for the debugging text to stop scrolling by. The final line of text should be:
Then, login using the user name and password from the PAP howto. (Which we assume you have already followed.) If all goes well, the server should send back an Access-Accept packet.
When the above method is used, the following authentication types should just work:
- PEAPv0
- EAP-GTC
- EAP-MSCHAPv2
- EAP-TTLS
- PAP
- CHAP
- MS-CHAP
- EAP-MD5
- EAP-MSCHAPv2
At this point, there are only a few things that can go wrong. See the EAP problems page for some common problems and solutions.
You can also enabled the Windows 802.1X trouble-shooting guide to see what Windows is doing.
Once this step works, you can proceed to creating the production certificates.
